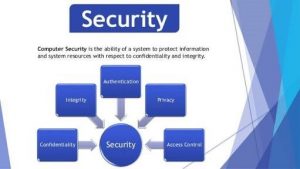
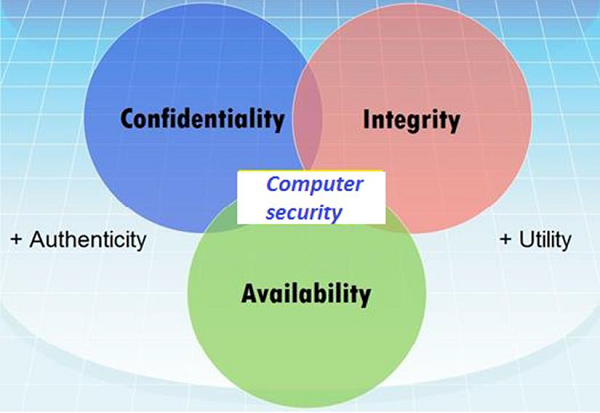
1 Computer System Security Tutorials | Introduction To Computer System Security | GeekySessioon - YouTube

The Human Factor in IT Security: How Employees are Making Businesses Vulnerable from Within | Kaspersky official blog
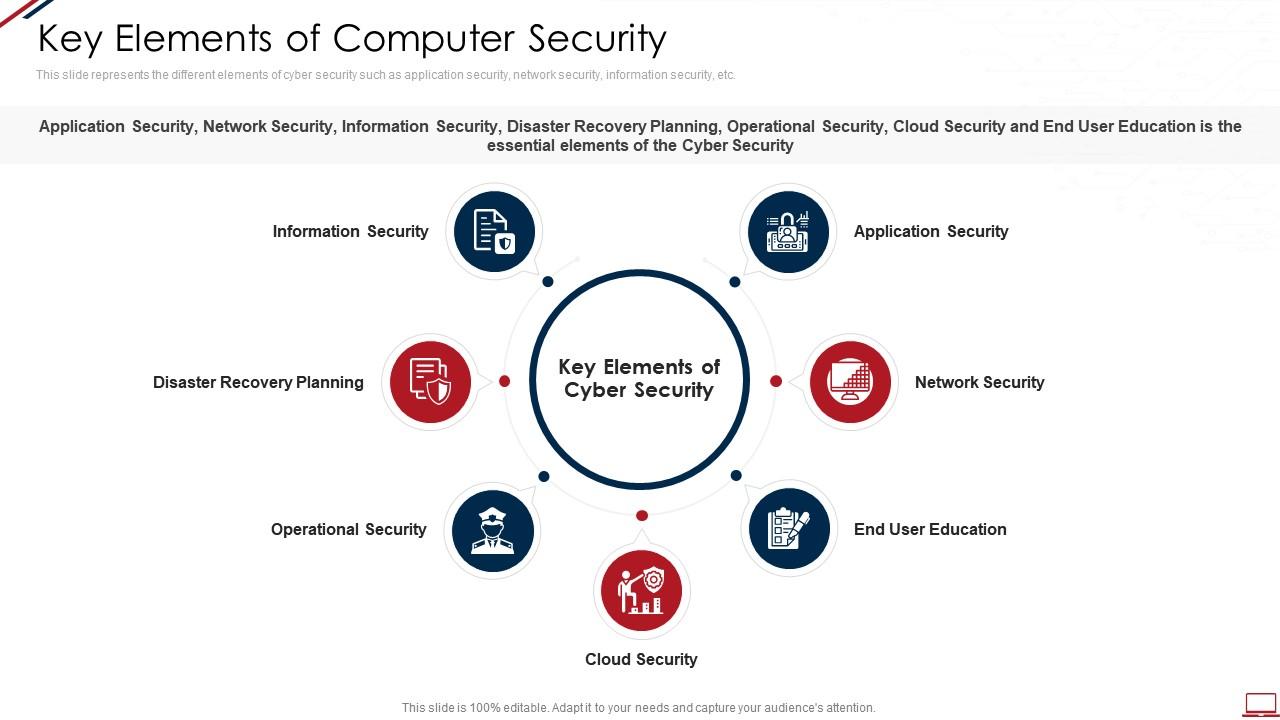
Computer System Security Key Elements Of Computer Security | Presentation Graphics | Presentation PowerPoint Example | Slide Templates